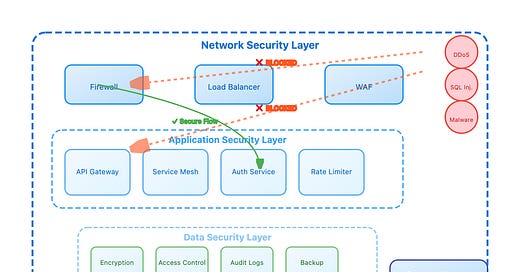
What We'll Learn and Demo Today
Our exploration covers three critical defensive layers that world-class distributed systems employ: Zero-Trust Network Architecture with mutual TLS authentication, Runtime Security Monitoring with behavioral anomaly detection, and Adaptive Threat Response with automated containment policies. You'll implement a complete security stack that demonstrates how these layers work together to create a system that's harder to compromise and faster to recover when attacks succeed.